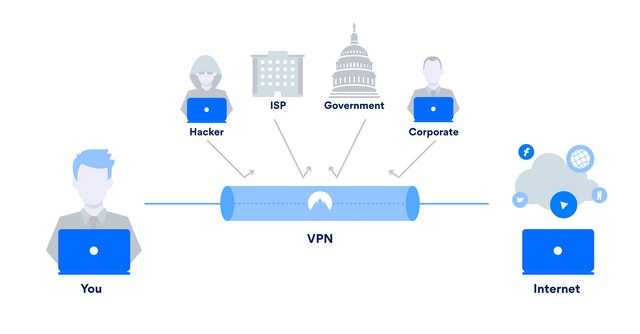
A VPN network (virtual private network or virtual private network) is a tunnel which unites us safely to another network. Further, the data is encrypted so that communications cannot be intercepted.
It is a form of a secure connection within an insecure environment, such as the Internet.
Is it secure communication?
All the information that is transmitted by that “virtual cable” or better called a tunnel. It is encrypted from end to end and is therefore secure.
Even when that VPN tunnel is created using Internet resources, it is a secure medium.
The VPN network offers us end-to-end encryption.
Although we connect through a public Wi-Fi, once the tunnel is established, communications will be transmitted securely (this does not exclude that other security factors should be considered). Besides, it is independent of the type of connections used to access.
You can establish the tunnels can with PCs and, of course, also with mobile devices.
There are numerous apps for both Android VPN and IOs. These devices connect against a VPN server, which can be a dedicated computer, a firewall, a router, etc.
VPN networks vs. Remote control software
VPN connections are sometimes confused with remote control programs.
Depending on the software used, they also allow secure access to remote resources. However, its applications and ways of working are very different.
With a remote control program, we can access our office equipment and use it as if we were in front of that equipment. The communication established should be safe too. Controlling the office equipment implies having a team in the office to connect.
The Advantages of Using VPNs
Securely access another network.
Especially useful in the case of mobile users (commercial, work from home …).
We want employees to be able to access files, applications, printers, and other resources in the office network.
As the company’s network is accessed by many, security must be fundamental.
We need a tunnel server in the office: Usually, the firewall or a team dedicated to these tasks.
And also, we need a VPN client on the user’s computer, which is going to connect: the most widespread is OpenVPN, which is available for all platforms (Windows, iOS, Android, Linux, etc.).
Connect several networks.
By joining the delegations, workers can use the resources interchangeably as if both offices were linked with a cable.
At the same time, the limitations, restrictions, access control, etc. that can be created in a conventional network can be established.
In this case, we need to create a VPN called: Site to site.
It is generated between 2 devices. Usually, between the firewalls or router of each office.
Maintain privacy if we connect to a public or untrusted network.
As are the Wifi access points of hotels and shops, it is an aspect Especially recommended for those people who move.
The most reasonable thing, when we go on a trip, is to look for available Wi-Fi networks. From them, we access our data: email, messaging programs, business applications, etc.
As of this circumstance, cybercriminals are also aware. It is one of the most common attack vectors:
Simulate legitimate networks to connect unsuspecting users and steal credentials, accesses, identities, browsing data, etc.
A good practice is to access our network via a VPN from that “Free Wifi.” From there, we will be connected to the office, and our Internet access will be that of our business (as safe or insecure as it is, of course).